To assist in safeguarding journalists from spyware on their devices, Reporters Without Borders (RSF) offers journalists a free service available in several cities around the globe that checks devices for signs of compromise by using the open-source tool SpyGuard.
The use of spyware against journalists is on the rise, particularly for those reporting on authoritarian regimes. While digital security tools such as DangerZone can help mitigate the risk of opening files, spyware can be installed remotely and offline, and is a particular risk when a journalist’s devices are seized by law enforcement. Digital attacks often go unnoticed, so it is vital that journalists regularly check if their devices are compromised.
Free-of-charge security checks around the world
This service is available free of charge in RSF HQ in Paris but also in several regional offices like Taipei, Tunis and Dakar. Rio de Janeiro and Washington D.C. will also soon provide the service. The Beirut Press Freedom Centre is also equipped with such devices and proposes free-of-charge services. The RSF section in Berlin offers an additional spyware detection service using a different tool.
All requests for device analysis must be made through RSF’s Assistance Department, which can be reached at assistance(at)rsf.org.
How SpyGuard works
- SpyGuard checks for signs of spyware. By analysing the internet traffic going to and from the device, much like an Internet Service Provider (ISP) would, SpyGuard can detect suspicious connections and identify potential indicators of compromise by spyware and other network anomalies.
- Analysis takes at least 10 minutes. Any suspicious internet traffic going to and from the device in that time will be picked up by SpyGuard and flagged as a potential “Indicator of Compromise” (IOC). Ten minutes is considered sufficient to take a “picture” of the device’s internet traffic.
- No personal data is collected except the WiFi access points the device was connected to. The SpyGuard station only captures network traffic, much like an ISP, and does not collect any other personal data nor install any software on the device.
How to interpret the results
- Green: no obvious indicator of compromise detected. However, this does not guarantee by 100% the device is free of malware: very sophisticated spyware may evade detection by disguising itself as legitimate network activity.
- Orange: moderate indicator of compromise detected. In such cases, some indicators like IP addresses using suspicious network protocols need an advanced analysis in order to remove doubts. The produced report can be sent to RSF cyber experts and/or the RSF Digital Security Lab (DSL) for further investigation to confirm any suspicious activity or any false positives.
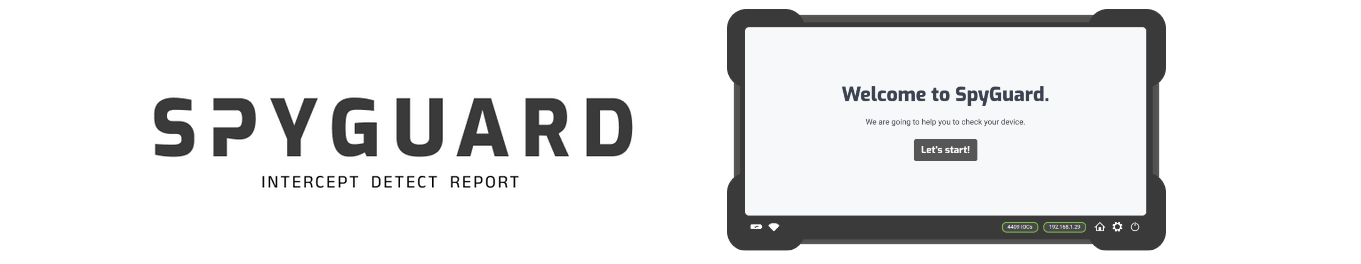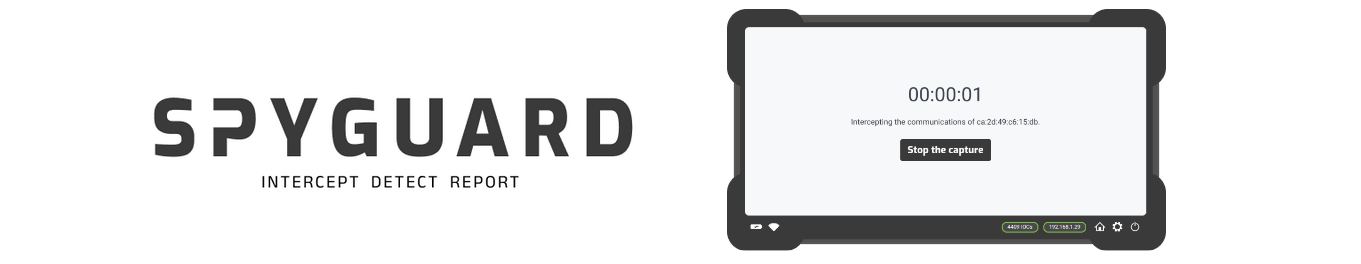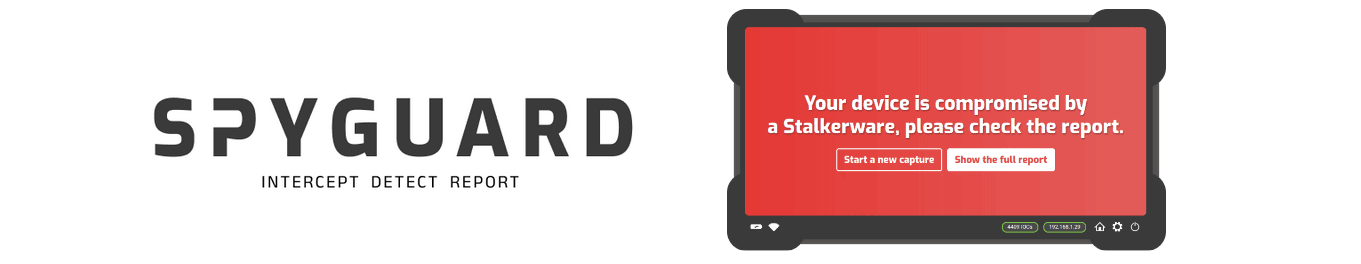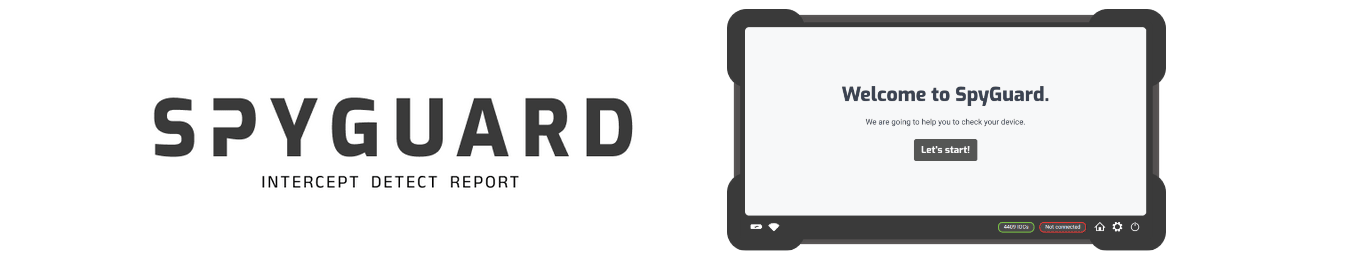
- Red: critical indicator of compromise detected. The device is likely compromised. Journalists are advised to immediately contact the RSF cyber experts and/or the RSF Digital Security Lab for investigation and cease using the device. Journalists should know that the DSL’s forensic analysis of their device will be much deeper and will also likely analyse their data and backups with the journalist’s consent.
Limitations of SpyGuard
- It can only detect malware that could be active during the analysis, based on a collection of Indicators of Compromise.
- It cannot detect if a journalist’s online accounts have been compromised, such as email and social media.
SpyGuard is only a detection tool, it cannot remove a spyware spotted so journalists should consider other forensic analysis and support for an advanced assessment and potential remediation.