Every journalist should use a VPN (Virtual Private Network) to hide their internet traffic, especially when sending sensitive information. However, finding a trustworthy VPN service provider can be challenging, especially when the service is free-of-charge. In this article, Reporters Without Borders (RSF) discusses what to look for when choosing a VPN.
In 2023, a major data leak involving SuperVPN and several other free-of-charge VPN apps compromised the personal data of over 360 million users-–including email addresses, device info, and online activities. For journalists, and anyone relying on a VPN (Virtual Private Network) to protect their digital footprint, this incident revealed a serious risk: that choosing an unreliable VPN service could be just as dangerous as not having one at all.
How ISPs see your online activity
Internet service providers (ISPs), as well as governments and potential malicious actors, can track and monitor the online activity of internet users. The ISP sees websites visited, time spent there, and the size of the data packets sent and received. Even with an encrypted website (URLs that start with https://), the ISP still receives the URL. Like a parcel delivery service, your ISP may not know what your data (package) contains, but they can see who sent it, where it goes, and how big it is.
A Virtual Private Network is a digital tool that hides a user’s activity in real time by creating an encrypted tunnel for data to travel through. Using a VPN is like switching to a different courier: the ISP no longer sees the final destination of the data; it only sees that it is going to the VPN provider. The VPN then forwards that package to its true destination. In theory, this protects your browsing from surveillance. But it also means your VPN is now fully responsible for ensuring your data’s privacy.
The hidden risks of free VPNs
Not all VPN services prioritise privacy. A large number of free VPN apps—including SuperVPN—are operated by companies based in China. These providers often have vague or misleading privacy policies, a lack of transparency about data collection, and may have ties to surveillance agencies.
The business model of free VPNs is itself a red flag; VPN providers need money to operate servers, develop software, and maintain security infrastructure. If the user is not paying for the product, then the user may be the product. Free VPNs have been found to monetise their users by selling their data, logging traffic, injecting ads, selling bandwidth, or even installing spyware.
What journalists should look for in a VPN
Journalists should evaluate any VPN carefully to make informed decisions that prioritise privacy and personal safety. Consider these five criteria:
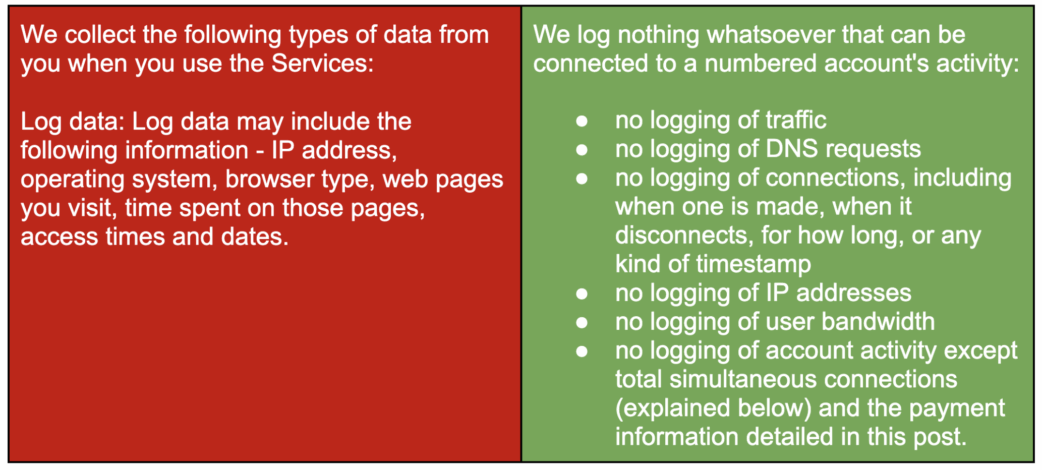
- Policy. A reliable VPN should have a clearly defined, independently verified, no-logs policy, meaning it does not collect or store information about your online activity. Avoid services that use vague language or state that they reserve the right to share data with third parties. Here are two fictional examples:
- Transparency. If a VPN is secretive about who runs it, that is a red flag. Trustworthy VPNs are open about their business practices, publicly disclose their ownership and partnerships, and publish regular transparency reports and independent security audits.
- Jurisdiction. Where a VPN is headquartered affects how it handles your data. Choose services based in countries with strong privacy protections and no laws requiring data retention, such as Switzerland or Sweden. Law enforcement in different countries will share information, so which jurisdiction is safe for you is highly contextual and depends on your personal situation and needs.
- Technical standards. A VPN should offer robust encryption, support secure protocols (such as WireGuard or OpenVPN with SHA-256 authentication; RSA-2048 or better handshake; AES-256-GCM or AES-256-CBC data encryption) and include essential features like a kill switch (a security feature that automatically disconnects your device from the internet if your VPN connection drops) and DNS leak protection. Open-source software allows the public to verify the tool’s security.
- Anonymity. An anonymous sign-up and payment option (e.g., cryptocurrency, cash, or gift cards) can be beneficial for users with privacy concerns.
Recommendations
There are too many VPN service providers to be all reviewed in this article, however, several providers stand out and meet the above criteria:
|
Criteria |
IVPN | Mullvad | |
|
Policy |
Minimum logging of user informations | Minimum logging of user informations | Minimum logging of user informations |
|
Transparency |
Regular independent audit & open source | Regular independent audit & open source | Regular independent audit & open source |
|
Jurisdiction |
Gibraltar | Sweden | Switzerland |
|
Technical standard |
Wireguard available | Wireguard available | Wireguard available |
|
Anonymity |
Accept cash or cryptocurrency | Accept cash or cryptocurrency | Accept cash or cryptocurrency |