Phishing scams are designed to trick people, and e […]
Recent Posts
Don’t get phished! Part 2: Introducing the five main phishing techniques
Phishing scams use deceptive messages to steal per […]
Don’t get phished! Part 1: What are phishing scams?
Phishing scams use deceptive messages to steal per […]
How to react if a military attack occurs
Learning how to cope with war scenarios is crucial […]
Prepare your bug-out bag in case of emergency
Journalists reporting in zones at risk must be pre […]
How to make a disaster response plan
Planning in advance safety protocols can help jour […]
Is cloud computing secure?
Cloud services such as Dropbox or Apple’s iCloud m […]
USB safety Part 2: Protect your USB port
The USB port, if left unsecured, provides an easy […]
USB safety Part 1: Use secure USB drives
USB drives are generally used without much concern […]
Five legal facts journalists should know when communicating online
Laws regarding a journalist’s freedom of expressio […]
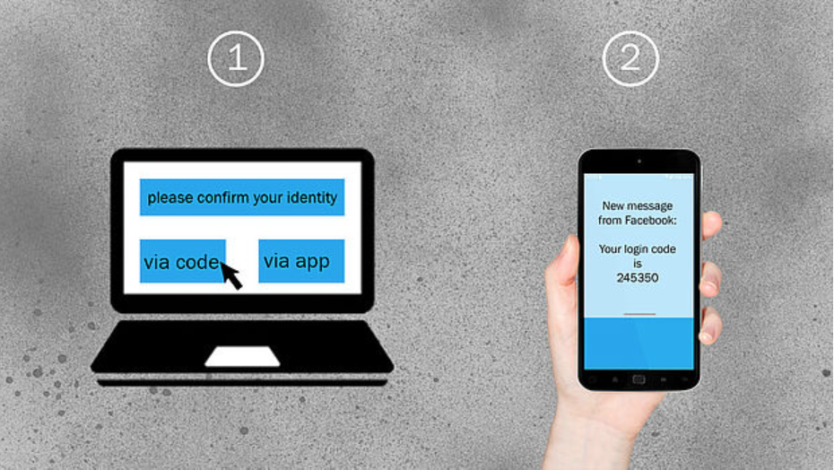
Two-factor authentication (2FA) to better protect digital accounts of journalists
Two-factor authentication (2FA) is the process of […]
A digital safety checklist for press photographers
Press photographers working with sensitive topics […]